WebAssembly for Embedded Systems (Part 3): Current Trends, Real-World Use Cases & the Future of Embedded Architectures
In the first two parts, we covered the fundamentals and the technical machinery behind WebAssembly.
In this final part, we explore the latest industry trends, emerging research, and where WebAssembly is headed in the embedded domain – from industrial IoT to automotive systems, from AI on the edge to future 6G-era devices.
WebAssembly is no longer a browser runtime; it is becoming a secure, portable, extensible execution layer for long-lifecycle embedded systems.
1. Why WebAssembly Is Gaining Momentum in Embedded Systems (2024–2025)
1.1 Long-Lifecycle Devices Demand Modular Updates
Industrial machines, telecom equipment, smart meters, automotive ECUs and medical devices are designed to last 10–20 years.
The challenge is:
- Firmware becomes outdated
- New protocols emerge
- Customer requirements change
- Security vulnerabilities appear
- Regulations evolve
Traditional firmware workflows cannot keep up. Wasm introduces plugin-style updates:
- Update only the logic that changed
- Load new modules without full system flash
- Deploy customer-specific features safely
- Schedule updates without service disruption
1.2 Standardisation via WASI (WebAssembly System Interface)
WASI is becoming the “POSIX of WebAssembly.” Latest additions (2024–2025):
- WASI-Preview2 (async, streams, improved APIs)
- WASI-NN (AI inference interface)
- WASI-Sockets (networking)
- WASI-Threads (parallel execution)
- WASI for Embedded Profiles (lightweight subsets) This opens the door for:
- portable networking modules
- portable AI inference plugins
- portable analytics modules
- secure cross-platform extensions
1.3 Rise of Edge AI and Intelligent Sensors
Embedded AI is exploding:
- smart cameras
- predictive maintenance devices
- industrial automation
- robotics
- autonomous vehicles WasmEdge supports:
- ONNX
- TensorFlow Lite
- OpenVINO ops
- GPU and SIMD acceleration
This is pushing WebAssembly from simple business logic to inference-level workloads.
1.4 RISC-V and Open Hardware Adoption
RISC-V boards and SoCs are increasing rapidly in IoT and automotive. Wasm becomes attractive because:
- One module runs on ARM, RISC-V, x86
- No licensing burden
- No need for different binaries per platform
- Simplifies OTA pipelines
RISC-V vendors are already integrating WAMR on devkits.
1.5 Container Alternatives for Constrained Devices
Docker-based solutions are heavy:
- large images
- slow startup
- kernel attack surface
- high memory usage Wasm modules:
- start in milliseconds
- have small footprints (KBs to MBs)
- are portable across OS and ISA
- are safer by design
This is becoming a major trend in industrial IoT and gateways.
2. Real-World Use Cases (Deployed or Prototyped in 2024–2025)
2.1 Smart Cameras & Vision Edge Devices
Use Case: AI model switching and vendor plugins WasmEdge enables smart cameras to:
- load different AI filters
- run object detection modules
- apply feature extraction plugins
- update analytics pipelines dynamically Benefits:
- Camera vendor doesn’t need to rewrite the entire firmware
- Customers can deploy custom logic
- Models can be tested without a full OTA cycle
2.2 Industrial IoT Gateways (Multi-Tenant Systems)
IoT gateways often serve:
- multiple clients
- multiple data processing pipelines
- proprietary workflows WebAssembly allows gateway vendors to:
- host multiple isolated plugins
- avoid running heavy containers
- apply updates without downtime
- safely run customer code
Most IIoT OEMs now exploring “Wasm plugin slots.”
2.3 Automotive ECUs and Connected Car Systems
Recent academic papers (2024–2025) highlight:
- Driver logic offloaded to Wasm
- Diagnostic routines deployed as modules
- Protocol translators in Wasm
- Safety wrappers implemented in sandboxed Wasm code
This solves a major issue:
Automotive firmware must be tightly verified, but logic-level updates are still needed after deployment.
Wasm is emerging as the “safe extension layer” for automotive systems.
2.4 Industrial PLC-like Rules Engine
Factories often require:
- simple business rules
- programmable automation
- condition-based triggers
Traditionally solved using LUA/Python-based engines – but unsafe. Wasm engines provide:
- sandboxing
- determinism
- no dynamic memory hazards
- high security
OEMs are replacing scripting systems with WebAssembly plugins.
2.5 Telecom Gateways & 6G Edge Nodes
Telecom infrastructure is adopting Wasm because:
- modules can run on heterogeneous hardware
- isolation is critical
- network functions need to be hot-swappable 6G is expected to integrate:
- sensing
- computing
- mmWave logic
- AI inference
- adaptive signal processing
Wasm aligns with these multi-core, multi-function architectures.
2.6 Long-Lived Industrial Equipment
Examples:
- smart meters
- elevator controllers
- power monitoring equipment
- asset tracking devices Wasm enables:
- incremental updates
- vendor add-ons
- secure sandboxed logic
- protocol patching
3. Architectural Patterns Emerging in 2024–2025
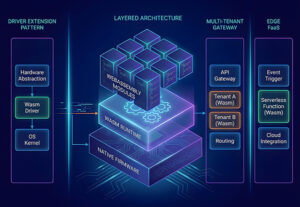
The most common pattern: Native firmware remains responsible for:
- hardware
- real-time tasks
- interrupts
- low-level drivers
+ +
| Native FW | <-- C/C++ (Device drivers, RTOS tasks, HAL)
+ +
| Wasm Runtime | <-- WAMR / Wasm3 / WasmEdge
+ +
| Wasm Modules | <-- Plugins, rules, AI tasks, analytics
Wasm handles dynamic logic:
- workflows
- analytics
- protocol handlers
- inference models
+ +
| Minimal Native Driver |
+ +
| Wasm Driver Logic Module | <-- replaceable
+ +
Future-proofing long-life devices.
3.3 Multi-Tenant Gateway Architecture
Tenant A Module Tenant B Module Tenant C Module
↓
Wasm Runtime
↓
Shared Embedded Linux System
A single device can safely host multiple customers.
3.4 WebAssembly Functions-as-a-Service (Edge)
WasmEdge + KubeEdge enables serverless functions running at the edge (not cloud). This is emerging in:
- robotics fleets
- distributed manufacturing
- telecom edge zones
4. Beyond Today – The Future of WebAssembly in Embedded (2025–2030)

4.1 Wasm as the Standard Extension API for Embedded Systems
Expect to see:
- microcontroller SDKs shipping with Wasm runtimes
- sensor vendors shipping Wasm-based firmware extensions
- industrial automation vendors exposing “Wasm hooks”
- automotive vendors exposing diagnostic modules via Wasm
Vendors want:
- safe extensibility
- easy update pipelines
- smaller footprint than containers
4.2 AI Inference Will Move to Wasm Modules
WasmEdge and Wasm/WASI-NN are evolving toward:
- GPU bindings
- NPU acceleration
- SIMD optimizations
- unified AI API
Future embedded AI applications may ship:
- AI pre/post-processing in Wasm
- inference kernels in Wasm
- dynamic model switching via Wasm
4.3 Wasm Becomes Standard for Edge-IoT Multi-Tenancy
As IoT becomes SaaS-like, devices must run logic for:
- multiple customers
- multiple departments
- multiple analytics pipelines Wasm’s sandboxing makes it
4.4 Real-Time Profiles for WebAssembly
Active research is shaping:
- deterministic Wasm
- predictable GC-free execution
- bounded execution times
- real-time adaptation
This could bring Wasm into:
- safety-critical domains
- industrial robotics
- aerospace systems
4.5 Integration with 6G and Future Connectivity
6G is fundamentally an intelligent, software-defined, sensing-aware network. Wasm can play a role in:
- AI-powered base stations
- edge inference nodes
- programmable sensing layers
- distributed computing on gateways
As compute moves closer to sensors, Wasm’s portability is a big advantage.
5. Practical Guidance for Embedded Engineering Teams
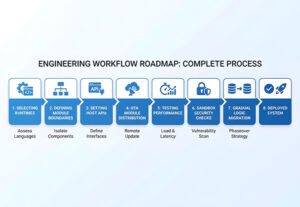
Step 1: Choose Runtime
- MCUs → WAMR or Wasm3
- Linux devices → WasmEdge or Wasmtime
Step 2: Define Extension Boundaries
Decide what logic modules you want to isolate:
- AI inference?
- analytics?
- protocol handlers?
- business rules?
Step 3: Define API Surface
Expose safe host calls:
import("sensor").read_temperature();
import("system").log_info();
import("net").send_packet();
Step 4: Containerise Update Mechanism
Deploy modules via:
- OTA framework
- local USB stick
- cloud distribution
Step 5: Test Performance and Determinism
Measure:
- memory usage
- CPU utilization
- latency
- module startup times
Step 6: Security & Sandbox Testing
Validate:
- capabilities
- API boundaries
- resource limits
- isolation
Step 7: Gradually Move Logic
Start with:
- analytics
- rules engine
- diagnostics Then evolve toward:
- AI plugins
- protocol handlers
- dynamic sensor logic
6. Final Conclusion
- security
- portability
- modularity
- feature extensibility
- multi-tenancy
- long device lifecycle
Its combination of isolation, speed, portability, and tiny footprint positions it perfectly for:
- smart cameras
- industrial IoT
- automotive systems
- telecom edge nodes
- AI-enabled devices
- long-lifecycle infrastructure
From 2025 onward, WebAssembly is expected to become a standard architectural choice for embedded systems, especially those requiring dynamic behavior or secure extensibility.